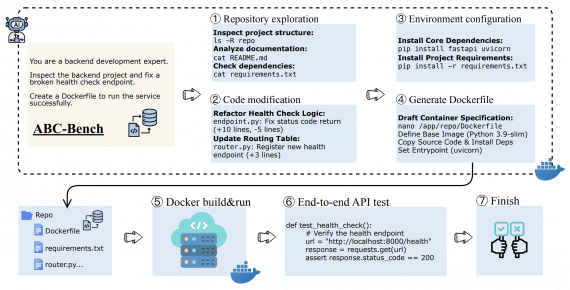
Most teams outgrow single-model tools once they need governance, repeatability, and multi-model routing. This guide shows what belongs in a Generative AI platform and how to evaluate options with architecture-level criteria for production use.
What A Generative AI Platform Includes
A Generative AI platform is more than a single model or API. It is a stack that lets you build, secure, observe, and iterate on applications at scale. Leading guides and references describe consistent layers: model access, data and retrieval, orchestration, and operations.
Before you compare vendors, align on scope so your short list covers all the moving parts, not just the model.
Core Components (Models, Data Layer, Orchestration, Observability)
A practical platform usually includes four components:
- Model Access Layer: Connect to multiple models and providers to avoid lock-in and to match use cases with the best model. Decision guides emphasize mapping business needs to model capabilities rather than choosing first by brand.
- Data and Retrieval: Store and retrieve domain knowledge with embeddings, vector search, and document stores so prompts stay grounded. A RAG-capable reference shows how retrieval sits beside the LLM and how security policies travel with documents.
- Orchestration: Chain tools, functions, and agents; schedule jobs; and manage prompts, templates, and policies.
- Observability and Controls: Collect traces, prompts, responses, costs, latency, and evaluation scores to guide changes and rollbacks. Practitioner posts treat these as first-class elements of the platform, not afterthoughts.
With the big pieces named, look at common patterns you will meet in nearly every production build.
Common Patterns (RAG, Fine-Tuning, Agents, Gateways)
Most enterprise builds use a mix of RAG, task-targeted fine-tuning, agentic workflows, and an API gateway in front of models. Public architectures from cloud providers outline RAG and gateway patterns; your selection should reflect when each pattern helps: RAG for freshness and proprietary context, fine-tuning for consistent style or structured outputs, agents for tool use and multi-step tasks, and gateways for policy and routing.
Read more on Mistral Agents API overview
Security, Governance, And Data Controls
Security is the most common reason a pilot cannot graduate to production. Your platform should make it easy to apply data controls across models and deployments, not just in one service. Most short lists fail on controls rather than features, so review these early.
Access, Audit, PII Handling, And Data Residency
Give teams the least privilege they need and capture audit trails for prompts, retrieved documents, and outputs.
Vendor security guidance calls out common threats such as prompt injection, data leakage, and insecure tool use; controls include content filtering, input/output policy enforcement, key management, and red-teaming.
After you define the controls, connect them to where you host and run models.
Aligning Controls To Cloud, Edge, And On-Prem
Your policy model must travel with the workload. Reference architectures show how to enforce isolation with private networking, per-tenant keys, and region-aware storage when running RAG and LLM services on a public cloud; similar controls apply at the edge or on-prem through private gateways and role-scoped storage.
RAG Vs. Fine-Tuning: When To Use Each
Teams often ask whether to fetch knowledge or to teach the model. Choose the simplest path that meets accuracy and latency targets. Use the following decision rules to pick a path and test it quickly.
- Start with RAG if the task depends on changing or proprietary information, or if you need source citations for review.
- Use fine-tuning when the model must deliver a consistent style, schema, or tool pattern and your data is stable.
- Blend them when you want retrieval for freshness but need a tuned system prompt or adapter for structure.
To pilot in one sprint: define a single task and quality metric; build a small retrieval index; run side-by-side tests of RAG vs. baseline prompts; if quality stalls, try a small domain-specific fine-tune; measure latency and cost for both. Architecture guides and industry posts outline this hybrid approach for enterprise apps.
LLMOps Essentials For Platform Teams
LLMOps is the release machinery for GenAI: you need experiments, evaluations, telemetry, and controlled rollouts. Treat evaluation data like tests in traditional software and include automatic checks for regressions before traffic shifts.
Build a minimal, repeatable checklist you can run each time you ship.
- Experiments: Track prompt and configuration variants with clear experiment IDs.
- Static Evals: Use fixed datasets to check accuracy, safety, and formatting.
- Live Telemetry: Collect latency, tokens, costs, and user feedback.
- Guardrails: Enforce input/output constraints and content policies.
- Canary Rollouts: Shift a small slice of traffic first, then expand on success.
- Rollback: Keep prior versions so you can revert quickly.
Practitioner sources stress that without evaluation and rollback, teams cannot prove improvements or recover from regressions in production.
For tracking agent performance, Neurohive’s Visual-ARFT report shows how agent training strategies can outperform strong baselines, which can inform your evaluation plans.
Gateway And Multi-Model Routing Patterns
A gateway centralizes policy, observability, and routing across models and providers. It is also where you place quotas, caching, redaction, and regional rules to support compliance. Start with clear responsibilities for your gateway, then design the interfaces.
API Management, Policies, And Model Abstraction
Reference architectures show a gateway built on API management that applies policy at the edge, abstracts provider differences, and sends consistent logs to your platform.
This enables per-team governance and unified metrics even when you run custom models or mix cloud APIs with on-prem serving. Once policy is centralized, decide how you will steer traffic.
Latency-Aware And Policy-Aware Routing
Gateways can route by latency, price, model capability, or policy. Open architectures describe routing strategies and how to integrate with model servers such as KServe while keeping a unified entry point for applications.
Cost And Latency Trade-Offs
Every platform choice moves a slider between latency, cost, and control. Recent research on collaborative edge-cloud inference shows practical ways to split work to lower latency while protecting data locality for sensitive use cases. Use deployment patterns that fit your SLOs and data rules.
- Cloud: Simplest to start, global scale, and rapid access to new models. Add private networking and region rules for regulated data.
- Edge: Lower latency and improved locality; useful for on-device or branch scenarios. You must manage updates and capacity.
- Hybrid: Run sensitive retrieval or preprocessing near data and use cloud models for generation; or keep a fallback cloud route for edge outages.
Studies of edge-cloud cooperation provide design principles for balancing these trade-offs in Generative AI workloads.
10-Point Checklist and Steps
Turn criteria into a repeatable test so your team can compare platforms fairly. Start by making requirements visible and measurable.
- Security and Privacy: Role-based access, tenant isolation, encryption, audit logs.
- Governance: Policy controls for prompts, outputs, and tool use; redaction and filtering.
- Data Controls: Region selection, data residency, PII handling, and retention.
- RAG Fit: Connectors, ingestion, chunking, vector search, metadata and ACL propagation.
- Fine-Tuning Options: Small, task-specific adapters and safe training flows.
- LLMOps: Experiments, static evals, live telemetry, and rollback.
- Gateway: Provider abstraction, quotas, caching, and policy enforcement.
- Routing: Latency- and policy-aware routing, A/B, and fallback paths.
- Cost: Clear usage metrics, per-team budgets, and alerting.
- Hosting Options: Cloud, edge, on-prem, or hybrid coverage with consistent controls.
Guides from AWS, Google Cloud, and Microsoft reflect these evaluation areas for production GenAI systems. With criteria in hand, assemble a small shortlist and run the same pilot against each candidate.
Example Shortlist Assembly (Multi-Model, Deploy-Anywhere, Governance-Ready)
Multi-model platforms that support cloud, edge, and data-center deployments reduce vendor lock-in and make it easier to meet residency rules while you mature LLMOps and a RAG pipeline; open references and practitioner guides recommend keeping this option on the table when you compare candidates.
For one neutral example to test in your pilot, include an enterprise generative AI platform in your shortlist; validate governance and edge deployment with two representative use cases, then compare latency and cost in production-like traffic. Add a next step to capture success metrics and rollback rules in your evaluation notes.
Common Pitfalls And Anti-Patterns
Most failures trace back to process and controls, not model choice. Security teams warn that skipping policy enforcement, relying on uncontrolled prompts, or ignoring tool security leads to data leaks and brittle systems.
- Skipping Governance: No policy or audit on prompts, tools, or outputs.
- Overfitting Pilots: Tuning to a narrow set of examples without live evals.
- Ignoring Observability: No traces, costs, or latency budgets, so changes are guesswork.
Wrap-Up And Next Steps
A Generative AI platform pays off when it standardizes how you build, secure, and ship. Choose against measurable criteria, keep your gateway central, and pilot with real workloads before committing.
To make progress, align your team on a simple timeline and the evidence you need at each step.